Forensic Innovations Inc announced on its blog that it has a tool that can identify headerless encrypted data, such as TrueCrypt volumes. It can’t.
Last week, Forensic Innovations Inc announced on its blog that it has a tool that can identify headerless encrypted data, such as TrueCrypt volumes. Yesterday, this story was picked up by Slashdot.
Good ciphers, like AES, output ciphertext that is computationally indistinguishable from random data. An encryption tool that properly implements such a cipher to generate headerless encrypted data will also produce output that is computationally indistinguishable from random data.
For Forensic Innovations Inc’s tool to work, it would have to be able to distinguish between random or pseudo-random data and the output of ciphers like AES. I ran a quick test to see whether it could. It can’t.
I downloaded a trial copy of FI TOOLS for Windows 2.23. I then generated two 10 MB files filled with pseudo-random data. I used a PowerShell script to do this:
$b = New-Object byte[] 1024
$fs = New-Object System.IO.FileStream "C:\Test\random-1.dat", Create
$r = New-Object System.Random
1..10240 | % {
$r.NextBytes($b)
$fs.Write($b, 0, 1024)
}
$fs.Close()
$fs = New-Object System.IO.FileStream "C:\Test\random-2.dat", Create
$r = New-Object System.Security.Cryptography.RNGCryptoServiceProvider
1..10240 | % {
$r.GetBytes($b)
$fs.Write($b, 0, 1024)
}
$fs.Close()
The first file, random-1.dat, is filled with pseudo-random data generated by the System.Random class from the Microsoft .NET Framework. This class provides a very weak random stream. It should be distinguishable from a truly random stream.
The second file, random-2.dat, is filled with pseudo-random data generated by the System.Security.Cryptography.RNGCryptoServiceProvider from the Microsoft .NET Framework. This class provides cryptographically strong pseudo-random data that should be computationally indistinguishable from truly random data.
Finally, I created a third file, random-3.dat, which was a 10 MB headerless TrueCrypt volume created using the default settings and using a strong random password.
Here is the result:
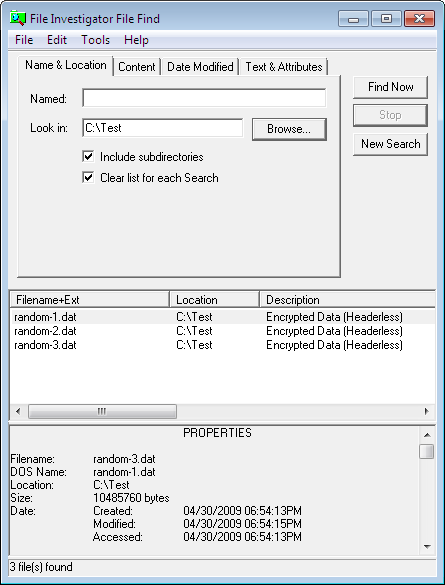
As you can see, the tool identified each of the files as headerless encrypted data. Only random-3.dat was actually headerless encrypted data. In other words, the tool cannot distinguish between pseudo-random data and headerless encrypted data.